Introduction
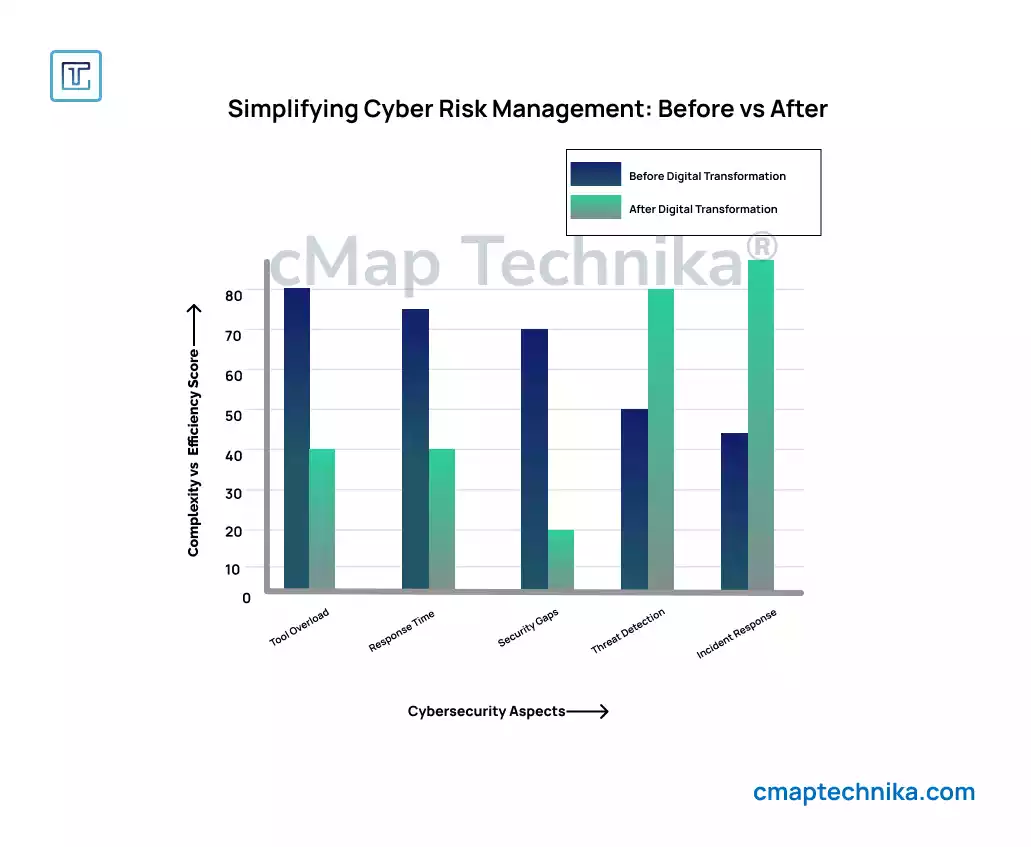
Cybersecurity has become a critical priority for modern businesses as the frequency and sophistication of cyber threats continue to rise. Data breaches, ransomware attacks, and insider threats pose significant risks to organizations, often leading to financial losses, reputational damage, and regulatory penalties. Despite investing heavily in cybersecurity tools and frameworks, many businesses struggle with managing cyber risks effectively due to the growing complexity of modern IT environments.
Managing cyber risk is not just about deploying more tools—it’s about simplifying security processes, improving visibility, and creating a cohesive strategy that aligns with business objectives. Overly complex security frameworks can create blind spots, increase response times, and overwhelm security teams. By adopting a streamlined, risk-based approach to cybersecurity, organizations can strengthen their defenses while reducing operational friction.
This guide outlines a step-by-step approach to reducing complexity in cyber risk management, helping businesses build a more resilient and agile security posture.
Step 1: Establish a Clear Cybersecurity Framework
The foundation of an effective cyber risk management strategy is a well-defined framework that aligns security efforts with business goals. Without a structured framework, security initiatives can become fragmented, leading to gaps in protection and inconsistent response capabilities.
How to Build a Strong Framework:
- Adopt a Recognized Standard:
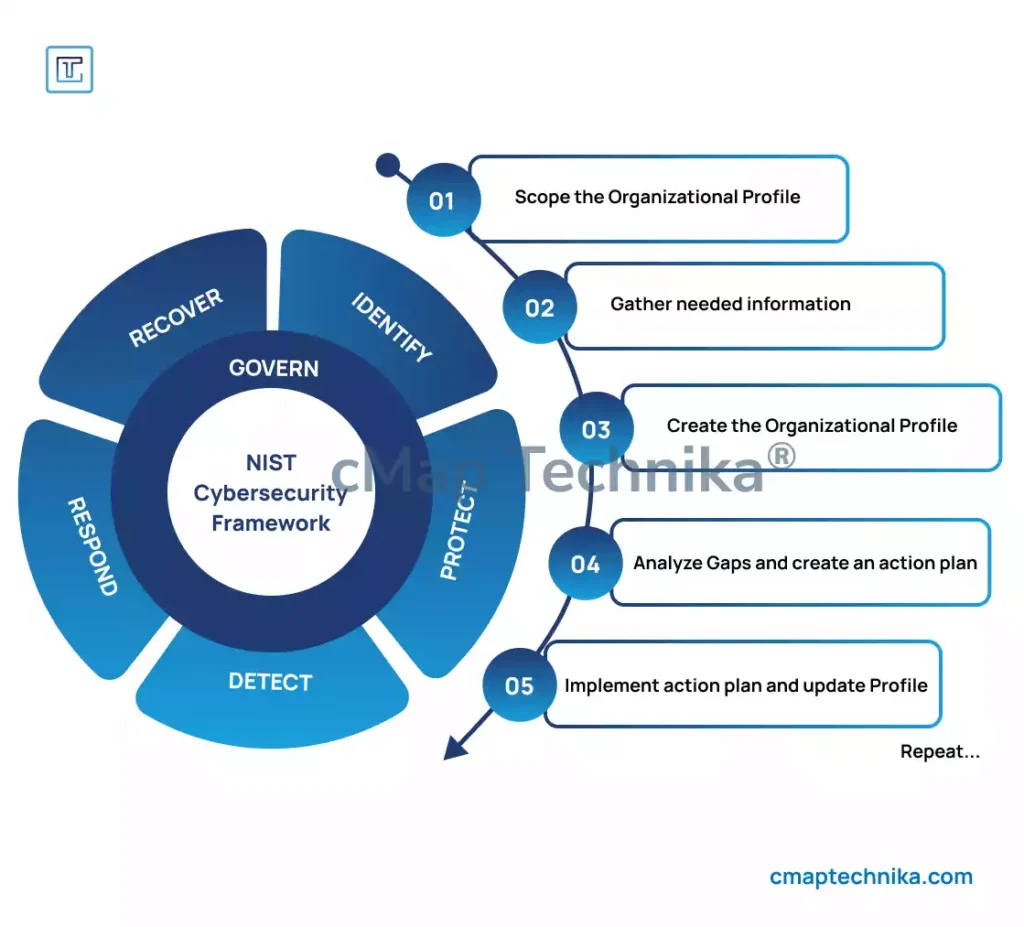
Implement industry-recognized frameworks such as the National Institute of Standards and Technology (NIST) Cybersecurity Framework, ISO/IEC 27001, or the Center for Internet Security (CIS) Controls. These frameworks provide a structured approach to identifying, protecting, detecting, responding to, and recovering from cyber threats.
- Define Business-Centric Objectives:
Align cybersecurity goals with business priorities. For example, if protecting customer data is a key objective, focus on strengthening data encryption, access controls, and endpoint protection. - Create a Centralized Policy:
Develop a single, cohesive security policy that outlines the organization’s approach to risk management, threat detection, incident response, and recovery. Ensure that all employees and departments understand and follow this policy.
Example:
JP Morgan Chase established a centralized cybersecurity framework based on the NIST model. By integrating security policies across all business units and automating threat detection, the company reduced its average incident response time by over 50%, strengthening its ability to respond to evolving cyber threats.
Step 2: Streamline Security Tools and Platforms
Many businesses accumulate a complex mix of security tools over time, leading to overlapping functions, fragmented reporting, and inconsistent threat detection. Consolidating and simplifying security platforms can improve visibility and response efficiency.
How to Reduce Tool Complexity:
- Conduct a Tool Audit:
Review all existing security tools to identify redundancies and gaps. Eliminate tools with overlapping functionality and focus on platforms that provide comprehensive protection. - Adopt a Unified Security Platform:
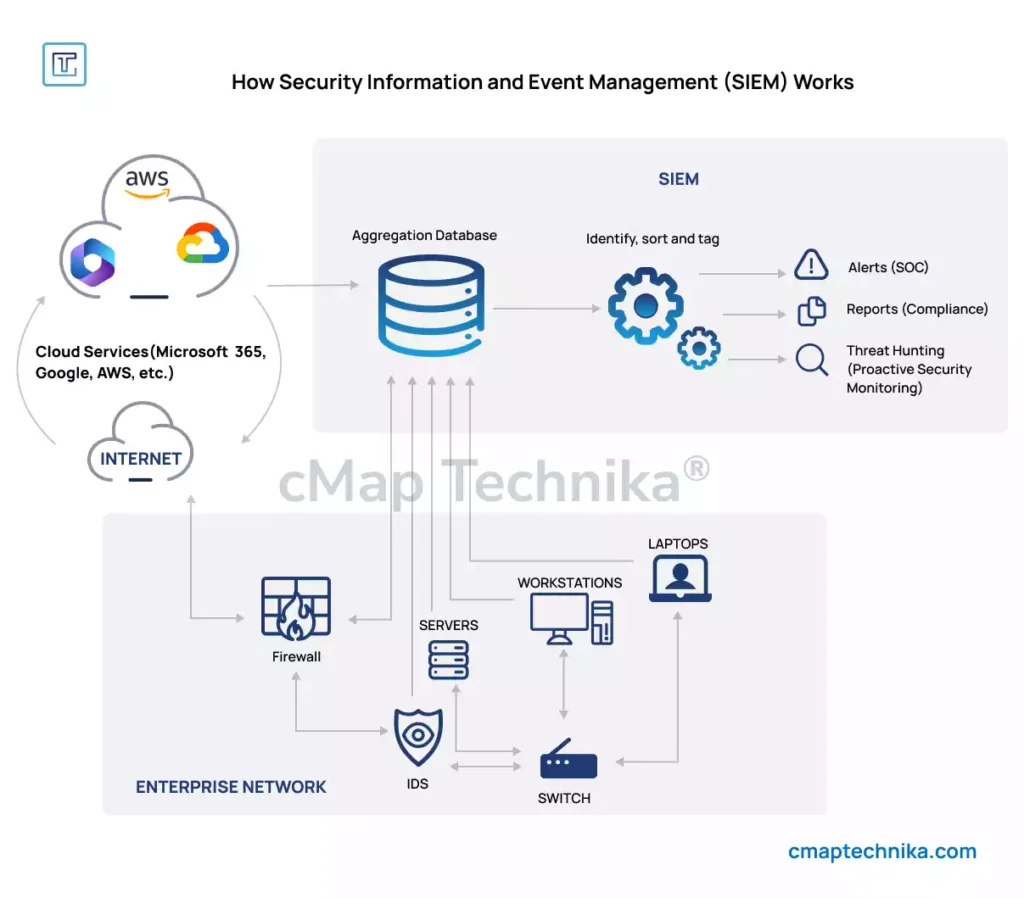
Use integrated security platforms (e.g., SIEM—Security Information and Event Management) that combine threat intelligence, incident detection, and automated response in one interface.
- Automate Routine Tasks:
Deploy automation for threat detection, patch management, and incident response to reduce the workload on security teams and improve response times.
Example:
Target consolidated its security operations into a single SIEM platform after suffering a major data breach in 2013. The unified platform enabled real-time threat detection and improved coordination between security teams, significantly reducing the time required to identify and mitigate threats.
Step 3: Focus on Risk-Based Prioritization
Not all threats are equal—focusing resources on high-risk areas helps organizations maximize protection while minimizing resource expenditure. A risk-based approach ensures that security efforts are targeted where they are most needed.
How to Prioritize Risks:
- Identify Critical Assets:
Map out business-critical systems and data, such as customer information, intellectual property, and financial data. Focus on securing these high-value targets first. - Use Threat Modeling:
Identify potential attack vectors and assess the likelihood and impact of each threat. Focus on threats with the highest business impact. - Implement Tiered Protection:
Establish multi-layered defenses, including firewalls, endpoint detection, data encryption, and zero-trust network access (ZTNA) for sensitive systems.
Example:
British Airways faced a data breach in 2018 that compromised the personal data of over 400,000 customers. In response, the company implemented a risk-based strategy, focusing on encrypting payment data and strengthening network segmentation to prevent future breaches.
Step 4: Strengthen Identity and Access Management (IAM)
A significant portion of cyberattacks involve compromised credentials and unauthorized access. Improving identity and access management helps prevent insider threats and unauthorized external access.
How to Strengthen Access Controls:
- Implement Multi-Factor Authentication (MFA):
Require multiple forms of verification for all system logins, including biometric authentication and one-time passcodes. - Use Role-Based Access Controls (RBAC):
Grant access based on the user’s job function. Limit administrative privileges to only those who absolutely need them. - Monitor User Behavior:
Use AI-driven analytics to detect anomalies in user behavior, such as unusual login locations or access to restricted files.
Example:
Google eliminated password-based logins for internal employees by adopting hardware-based security keys and biometric authentication. This strategy significantly reduced the risk of phishing and credential-based attacks.
Step 5: Build a Proactive Threat Response Strategy
A reactive approach to security is no longer enough. Businesses must establish real-time monitoring and automated response mechanisms to identify and mitigate threats before they escalate.
How to Improve Threat Response:
- Establish a Security Operations Center (SOC):
Create a centralized team responsible for threat detection, investigation, and response. Equip the SOC with real-time monitoring tools and AI-based threat intelligence. - Use Automated Incident Response:
Implement automated playbooks to handle routine security incidents such as failed login attempts, phishing attempts, and malware detections. - Conduct Regular Simulations:
Perform penetration testing and red team exercises to identify weaknesses and improve response coordination.
Example:
Microsoft implemented an AI-powered threat detection and response system that reduced the company’s average threat detection time from hours to seconds. The system automatically identifies and isolates compromised endpoints, preventing the spread of attacks.
Step 6: Educate and Empower Employees
Human error remains one of the biggest vulnerabilities in cybersecurity. Equipping employees with the knowledge and tools to identify and respond to threats strengthens the organization’s overall security posture.
How to Build a Security-Aware Culture:
- Provide Ongoing Training:
Conduct regular cybersecurity training covering phishing detection, password management, and secure data handling. - Create Clear Reporting Channels:
Make it easy for employees to report suspicious activity through a dedicated security hotline or email. - Enforce Accountability:
Hold employees and teams accountable for following security protocols. Recognize and reward good security practices.
Example:
IBM implemented a “cybersecurity boot camp” for all employees, providing hands-on training in identifying and responding to phishing attempts. Following the program, employee-reported phishing attempts increased by 40%, improving overall threat detection.
Conclusion
Simplifying cyber risk management is not about reducing protection—it’s about creating a streamlined, effective security strategy that enables faster threat detection, improved response times, and stronger overall resilience. Businesses that consolidate security tools, adopt a risk-based approach, and strengthen access controls can significantly reduce the complexity of managing cyber threats.
By investing in employee training, automation, and integrated platforms, organizations can enhance their security posture while reducing operational friction. Cybersecurity is no longer just a technical issue—it’s a strategic imperative. Businesses that simplify and strengthen their cyber defenses will be better positioned to protect sensitive data, maintain customer trust, and thrive in an increasingly complex threat landscape.






