In 2024, cybercriminals escalated their attacks, exposing vulnerabilities in some of the world’s most secure organizations. High-profile data breaches not only made headlines but also served as critical lessons in cybersecurity, highlighting the need for businesses to reassess their strategies to protect sensitive information. At WaltCorp, we’ve analyzed these breaches to uncover key insights that can help organizations enhance their security posture and avoid similar risks.
In this article, we’ll dive into the biggest data breaches of 2024, explore the lessons learned, and discuss actionable steps businesses can take to protect their data in a rapidly evolving cyber threat landscape.
1. The Importance of Proactive Threat Detection
Several breaches in 2024 were the result of advanced persistent threats (APTs)—attacks that went unnoticed for months, allowing cybercriminals to siphon sensitive data over extended periods. One of the most significant breaches involved a global tech giant, where attackers exploited a vulnerability in an outdated system, going undetected for nearly six months.
Lesson: Organizations must implement advanced threat detection systems that use machine learning and AI to identify unusual activity in real time. Early detection is crucial in mitigating the impact of a breach and preventing attackers from accessing or exfiltrating critical data.
Actionable Step: Invest in continuous monitoring tools that utilize AI to detect anomalous patterns and behaviors, enabling a quicker response to potential threats.
2. Zero Trust Architecture Is No Longer Optional
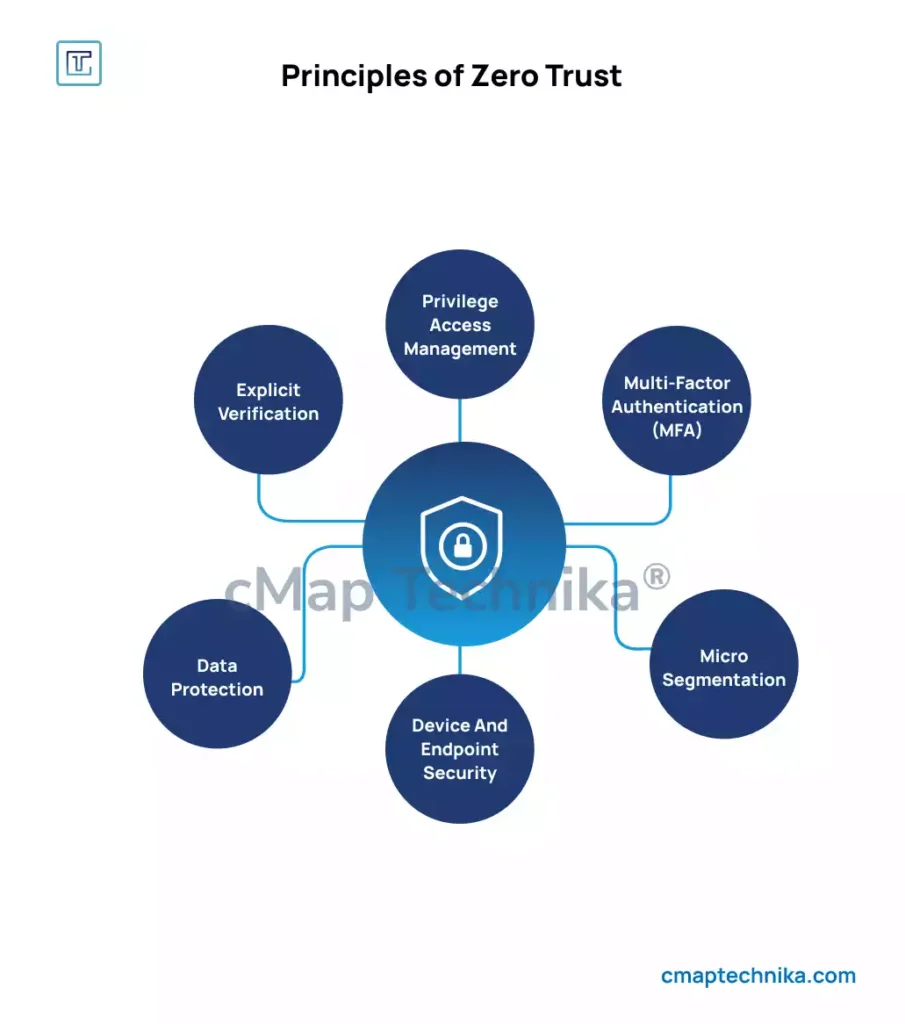
A major breach in the financial sector in 2024 exposed the vulnerabilities of traditional perimeter-based security models. Cybercriminals used stolen credentials to bypass security protocols, gaining unauthorized access to sensitive customer data. The breach highlighted the flaws in the outdated “trust but verify” approach, where once an entity is inside the network, it is often assumed to be trustworthy.
Lesson: Adopting a zero-trust security model—where every user and device is verified continuously—can significantly reduce the risk of internal and external threats.
Actionable Step: Implement a zero-trust framework across your network, ensuring that every user, device, and application is subject to rigorous authentication and access controls. This minimizes the potential for unauthorized access.
3. Ransomware Remains a Critical Threat
Ransomware attacks continued to evolve in 2024, with several high-profile cases targeting healthcare and energy sectors. Attackers not only encrypted critical data but also threatened to release sensitive information unless a ransom was paid. This trend shows how ransomware attacks are becoming more targeted and devastating, especially for organizations handling sensitive personal or financial data.
Lesson: Ransomware attacks are more sophisticated than ever, making it essential for businesses to have a robust incident response plan in place, along with proactive measures like regular backups.
Actionable Step: Develop and test a comprehensive ransomware response plan that includes regular backups, network segmentation, and training employees to recognize phishing attempts. Ensure backups are stored offline and are easily accessible in the event of an attack.
4. Weak Third-Party Vendor Security
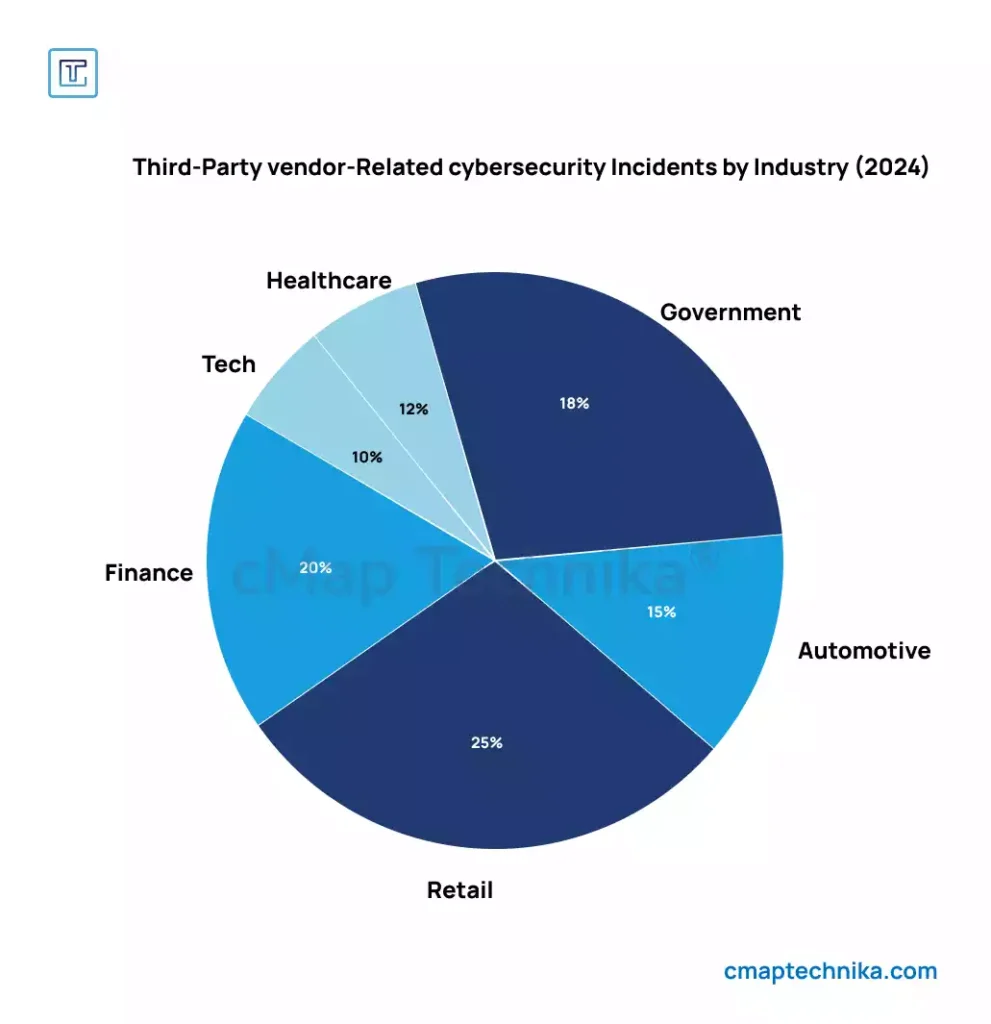
Another major breach in 2024 involved a supply chain attack, where cybercriminals targeted a third-party vendor to infiltrate a large multinational corporation. The breach compromised personal data from millions of customers and demonstrated the significant risks posed by weak security in third-party relationships.
Lesson: Organizations must extend their cybersecurity efforts to include third-party vendors and partners. A breach in your vendor’s system can have a devastating impact on your business.
Actionable Step: Conduct thorough security assessments of all third-party vendors, ensuring they adhere to your organization’s security standards. Use contract clauses that require vendors to maintain specific security protocols and inform you of any breaches.
5. Data Encryption: A Must-Have
Several breaches in 2024 involved unencrypted data being exposed to attackers, leaving sensitive information vulnerable. In some cases, attackers used stolen credentials to access databases containing vast amounts of unencrypted personal, financial, and medical data.
Lesson: Data encryption is essential for safeguarding sensitive information. Even if an attacker gains access to a system, encrypted data will be much harder to exploit.
Actionable Step: Ensure that all sensitive data is encrypted both at rest and in transit. Implement end-to-end encryption for communications and data storage, and invest in encryption keys that are regularly rotated and securely stored.
6. Employee Training and Awareness Are Critical
Despite the advanced technology employed by attackers, many breaches in 2024 began with simple human error—such as falling for phishing attacks or using weak passwords. One of the largest breaches involved a major retailer where attackers gained access through a spear-phishing campaign aimed at employees.
Lesson: Cybersecurity is not just about technology; it’s also about people. Employees are often the first line of defense, and a lack of awareness can leave organizations vulnerable.
Actionable Step: Implement regular cybersecurity awareness training for all employees, focusing on recognizing phishing attempts, creating strong passwords, and understanding the importance of data security. Conduct phishing simulations to reinforce these lessons.
7. The Need for Rapid Incident Response and Transparency
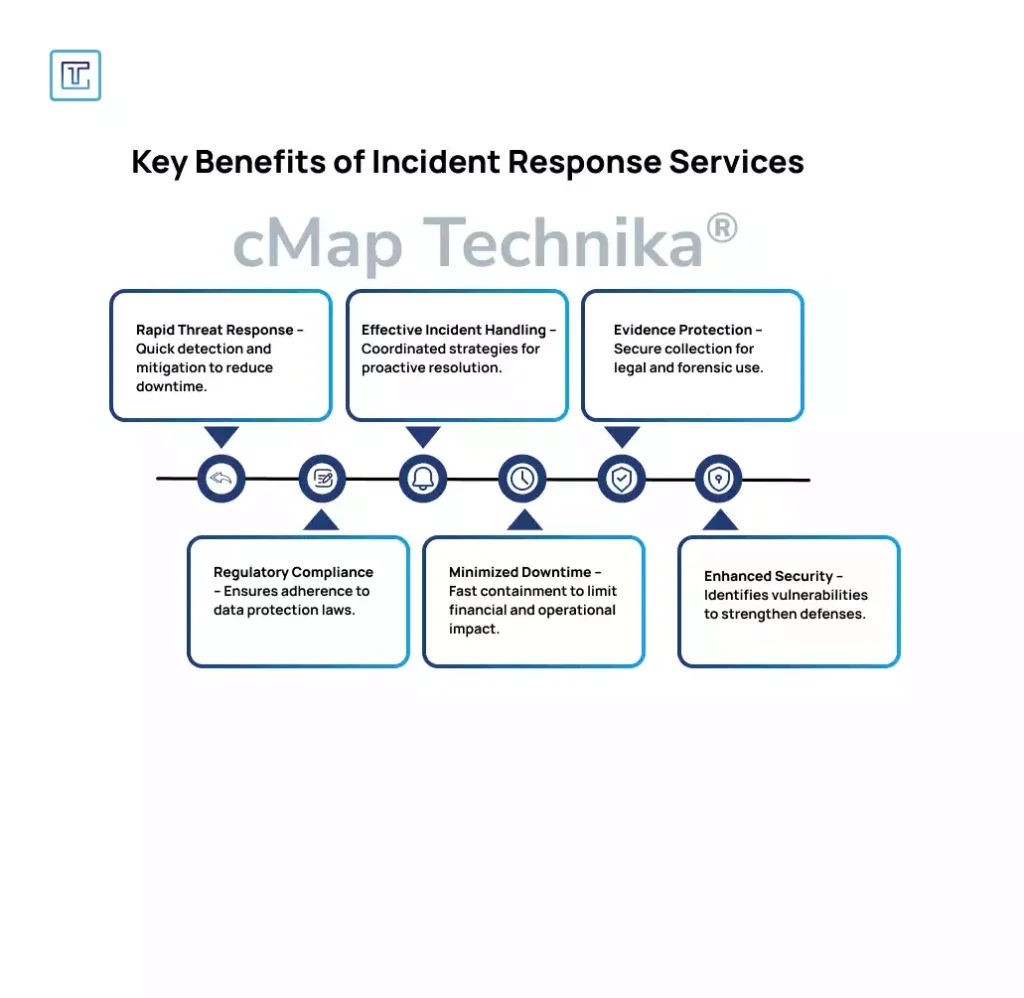
One of the most notable lessons from the 2024 data breaches was the importance of having a clear and rapid incident response strategy. A global healthcare provider faced a significant breach, but its response was slow, leaving customers in the dark about the extent of the damage for weeks.
Lesson: A timely, transparent response to a data breach is essential to maintaining customer trust and minimizing damage. The longer it takes to respond, the higher the reputational and financial impact.
Actionable Step: Develop an incident response plan that outlines clear roles, communication protocols, and timelines for detecting, containing, and mitigating the effects of a breach. Ensure transparency by notifying affected individuals and regulatory bodies as quickly as possible.
Conclusion
The biggest data breaches of 2024 have provided invaluable insights into the evolving nature of cyber threats and the lessons businesses must learn to strengthen their cybersecurity defenses. By investing in proactive threat detection, adopting zero-trust security models, securing third-party relationships, encrypting sensitive data, training employees, and responding swiftly to incidents, organizations can better protect themselves against future breaches.
At WaltCorp, we help businesses navigate the complexities of cybersecurity, offering tailored consulting services to strengthen your security posture and prepare for emerging threats. Let these lessons guide your strategy and help you safeguard your organization in an increasingly hostile cyber environment.






