As we move further into the digital age, the cybersecurity landscape continues to evolve rapidly. With the rise of new technologies, the increasing sophistication of cyber threats, and the expanding digital footprint of organizations, the need for robust cybersecurity strategies has never been more critical. As we approach 2025, businesses and individuals alike must prepare for the emerging trends and challenges that will shape the future of cybersecurity.
At WaltCorp, we stay ahead of the curve by closely monitoring developments in the cybersecurity sector and advising organizations on how to protect their digital infrastructure. In this article, we’ll explore the key cybersecurity trends and technologies expected to define the landscape in 2025, helping businesses understand what they need to prioritize to stay secure.
1. The Rise of AI-Powered Cyber Attacks
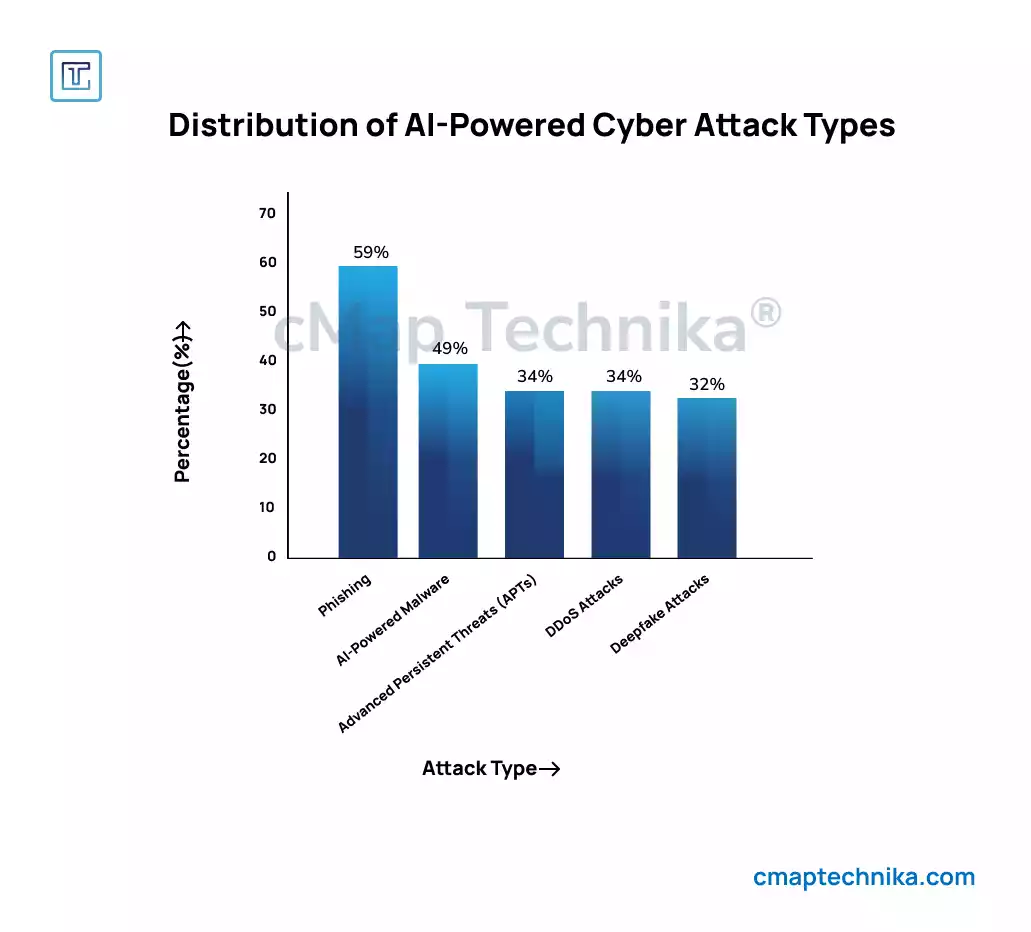
Artificial Intelligence (AI) is already revolutionizing cybersecurity, both in terms of defense mechanisms and cybercriminal activities. As AI continues to evolve, attackers are increasingly using AI tools to automate and enhance their cyber-attacks. These AI-driven attacks can adapt to and bypass traditional security systems, learning from failed attempts and becoming more sophisticated over time.
AI-powered attacks, such as deepfake technology and automated phishing campaigns, are expected to become more prevalent by 2025. These attacks are designed to deceive individuals into revealing sensitive information or infecting systems with malware without detection.
To counteract these advanced threats, organizations must deploy AI-driven defense mechanisms that can predict, detect, and respond to threats in real-time. Machine learning algorithms will play a critical role in identifying unusual patterns and blocking malicious activities before they cause significant damage.
2. Zero-Trust Security Models
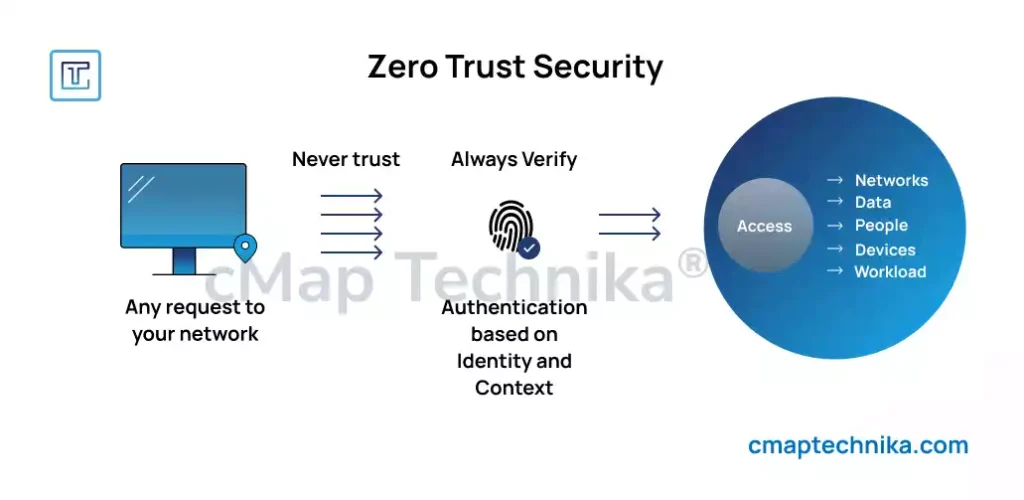
The concept of zero-trust security, which assumes no user or device—whether inside or outside the organization—is inherently trusted, is gaining significant traction in 2025. With the rise of remote work, cloud computing, and the Internet of Things (IoT), traditional perimeter-based security models are no longer sufficient.
Zero-trust models require continuous authentication and authorization of users, devices, and applications, ensuring that access to critical data and systems is strictly controlled. By adopting zero-trust principles, businesses can limit the impact of a potential breach and reduce the risk of internal threats, whether intentional or accidental.
As data breaches continue to increase, implementing a zero-trust architecture will become a critical strategy for safeguarding sensitive information and minimizing attack surfaces.
3. 5G and IoT Vulnerabilities
The widespread rollout of 5G networks and the increasing number of connected devices through the Internet of Things (IoT) are creating new vulnerabilities that cybercriminals are eager to exploit. In 2025, the convergence of 5G and IoT will present opportunities for cyber attackers to launch large-scale attacks, disrupting critical infrastructure and collecting vast amounts of personal data.
With 5G networks offering faster speeds and broader connectivity, attackers could target vulnerabilities in IoT devices such as medical devices, smart homes, and autonomous vehicles. Securing these devices will be crucial to mitigating the risks of cyber-attacks.
Businesses must prioritize cybersecurity measures in the design, development, and deployment of IoT devices and ensure that they are integrated into a larger, holistic security framework. Additionally, securing 5G networks will require more advanced encryption techniques and real-time threat monitoring to prevent malicious activities.
4. Ransomware 2.0: Sophisticated and Disruptive Attacks
Ransomware attacks are not new, but by 2025, they are expected to become even more sophisticated and disruptive. Cybercriminals are already using ransomware-as-a-service, targeting businesses with more tailored and destructive attacks. In 2025, these attacks may expand to include not only encrypting data but also threatening to release sensitive or damaging information, increasing the pressure on victims to comply.
Organizations must invest in proactive cybersecurity strategies, such as regular data backups, robust network segmentation, and employee training on phishing attacks. Additionally, implementing multi-factor authentication (MFA) and monitoring for abnormal behavior across systems will help detect ransomware attacks before they cause widespread damage.
5. Cloud Security and Data Privacy Challenges
As businesses continue to migrate to the cloud, cloud security remains a top priority. In 2025, securing cloud environments will require more sophisticated techniques to protect data from breaches and maintain compliance with data privacy regulations.
Hybrid cloud environments, which combine both public and private cloud infrastructures, are expected to become more prevalent. These environments can increase complexity in managing security controls, leading to challenges in protecting sensitive data across multiple platforms.
Organizations must adopt a multi-layered approach to cloud security, including data encryption, secure access controls, and continuous monitoring. Additionally, privacy regulations such as GDPR and CCPA are likely to become more stringent, requiring organizations to ensure that they meet compliance requirements and protect user data from exposure.
6. The Growing Importance of Cybersecurity Skills
As the digital landscape evolves, the demand for cybersecurity professionals will continue to rise. By 2025, the shortage of skilled cybersecurity experts is expected to be even more pronounced, with businesses struggling to find qualified personnel to protect their growing digital infrastructures.
To address this skills gap, organizations will need to invest in training and upskilling their current workforce. In addition, collaboration between businesses, educational institutions, and government agencies will be crucial to fostering the next generation of cybersecurity talent.
Furthermore, businesses should consider automating routine cybersecurity tasks, leveraging AI and machine learning to enhance their defense capabilities and reduce the reliance on human intervention for basic security operations.
7. Quantum Computing and Cybersecurity
Though still in its early stages, quantum computing is expected to have a profound impact on cybersecurity by 2025. Quantum computers will possess the ability to break traditional encryption methods, rendering current data protection protocols obsolete.
To prepare for this eventuality, researchers and cybersecurity experts are working on quantum-resistant encryption methods that can withstand the computational power of quantum computers. Organizations must stay informed about developments in quantum computing and begin transitioning to more secure cryptographic systems before quantum-powered attacks become a reality.
Conclusion
The cybersecurity landscape in 2025 will be defined by increasingly sophisticated threats and the emergence of new technologies that can either enhance or undermine security efforts. AI-powered attacks, zero-trust security, the vulnerabilities introduced by 5G and IoT, and the growing importance of cloud security will be among the top concerns for businesses.
To stay ahead of these challenges, organizations must adopt proactive cybersecurity strategies, invest in advanced technologies, and foster a culture of continuous improvement. At WaltCorp, we help businesses navigate the evolving cybersecurity landscape and implement effective strategies to safeguard their digital assets in an increasingly complex environment.






