Introduction
Infrastructure as Code (IaC) has emerged as a critical component of modern DevOps practices, enabling organizations to automate infrastructure provisioning, improve consistency, and accelerate deployment cycles. By defining infrastructure configurations as code, businesses can manage, modify, and deploy infrastructure components in a repeatable and scalable manner.
This guide outlines a structured approach to implementing IaC using industry-standard tools such as Terraform and Ansible. It will cover the benefits of IaC, key tools, and detailed steps to set up and manage infrastructure effectively. Following this approach can reduce human error, increase efficiency, and create more resilient systems.
Why Infrastructure as Code (IaC) Matters
Traditionally, infrastructure provisioning was a manual and error-prone process, requiring system administrators to configure servers, networks, and storage manually. This led to inconsistencies, longer deployment cycles, and increased operational risk.
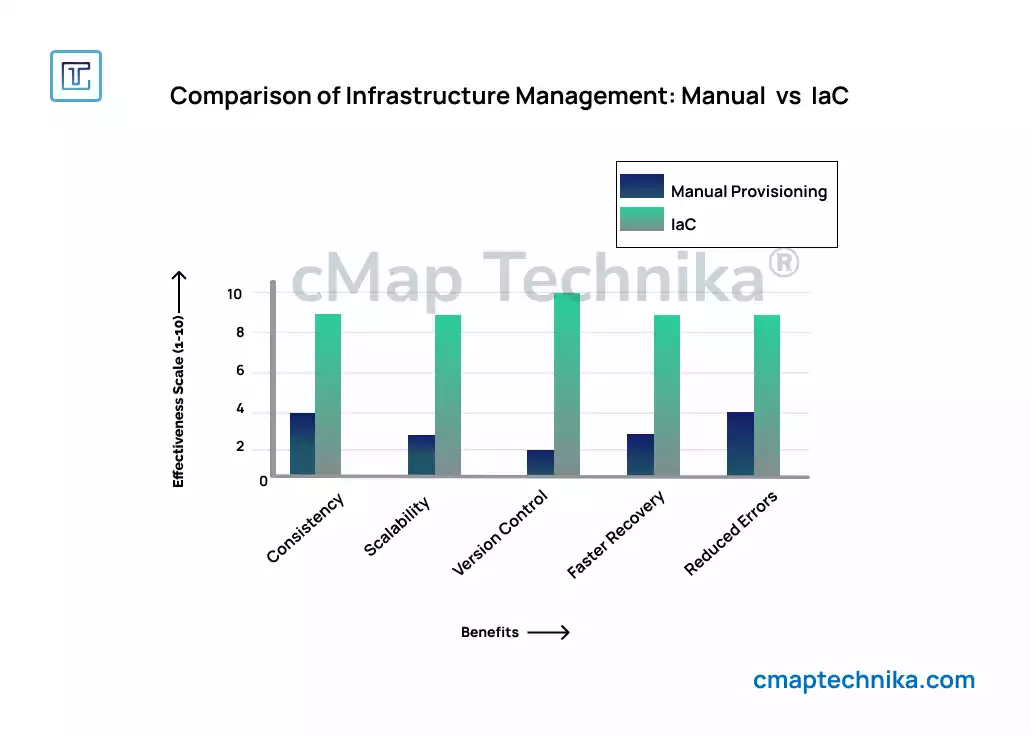
IaC transforms infrastructure management by treating infrastructure as code—using scripts and configuration files to automate provisioning and management. The key benefits include:
- Consistency: Code-based configurations ensure uniform deployments across environments.
- Scalability: Automated provisioning allows rapid scaling to meet changing demands.
- Version Control: Infrastructure changes can be tracked, audited, and rolled back using Git or other version control systems.
- Faster Recovery: Automated provisioning enables quick infrastructure redeployment.
- Reduced Errors: Automated testing and validation minimize human error and misconfiguration.
Key Tools for Implementing IaC
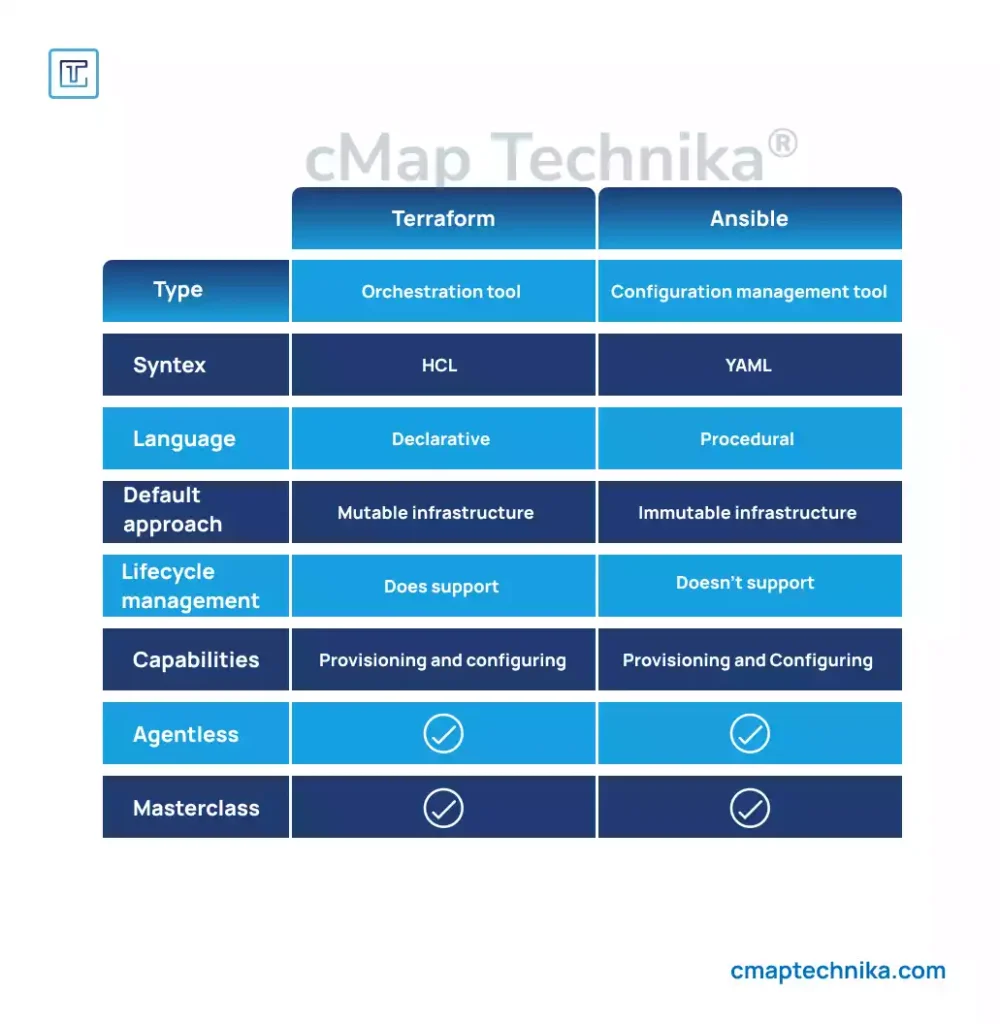
Two widely used tools for IaC are Terraform and Ansible. Each serves a different but complementary purpose:
1. Terraform – Infrastructure Provisioning
Terraform, developed by HashiCorp, is a declarative tool that enables infrastructure as code for cloud and on-premise infrastructure. It allows defining infrastructure using a high-level configuration language and deploying it across multiple cloud providers.
- Cloud Agnostic: Works with AWS, Azure, GCP, and on-premise solutions.
- State Management: Maintains infrastructure state and tracks changes for incremental updates.
- Declarative Approach: Ensures the actual infrastructure matches the defined state.
2. Ansible – Configuration Management
Ansible, developed by Red Hat, is an automation tool focused on configuration management and application deployment. It defines system configurations using YAML-based playbooks.
- Agentless: No need to install agents on target machines.
- Idempotent: Ensures repeatable playbook execution without unintended side effects.
- Simple Syntax: Uses human-readable YAML files for configuration and automation.
Step-by-Step Guide to Implementing IaC
This guide outlines a structured approach to implementing IaC using Terraform and Ansible.
Step 1: Set Up Your Environment

Before starting, ensure that your system meets the necessary requirements:
- Install Terraform and Ansible on your local machine.
- Configure access to cloud providers (AWS, Azure, GCP) using access keys or service accounts.
- Set up a version control system (Git) to manage infrastructure code.
Example: Installing Terraform and Ansible on Linux:
# Install Terraform
wget https://releases.hashicorp.com/terraform/1.2.3/terraform_1.2.3_linux_amd64.zip
unzip terraform_1.2.3_linux_amd64.zip
sudo mv terraform /usr/local/bin/
# Install Ansible
sudo apt update
sudo apt install ansible
Step 2: Define Infrastructure Using Terraform
Create a Terraform configuration file (main.tf) to define the infrastructure resources.
Example: Creating an AWS EC2 instance with Terraform:
provider “aws” {
region = “us-east-1”
}
resource “aws_instance” “example” {
ami = “ami-0c55b159cbfafe1f0”
instance_type = “t2.micro”
tags = {
Name = “example-instance”
}
}
Run the following commands to apply the configuration:
terraform init
terraform apply
Terraform will create the EC2 instance and maintain the state using a state file (terraform.tfstate).
Step 3: Automate Configuration with Ansible
Once the infrastructure is provisioned, use Ansible to configure the system and install necessary applications.
Example: Creating an Ansible playbook (setup.yaml) to install NGINX:
– name: Install NGINX
hosts: all
become: yes
tasks:
– name: Install NGINX
apt:
name: nginx
state: present
Run the playbook:
ansible-playbook -i inventory setup.yaml
Ansible will configure the EC2 instance and install NGINX.
Step 4: Use Git for Version Control
Store Terraform and Ansible files in a Git repository for version control and collaboration.
git init
git add .
git commit -m “Initial commit”
git push origin main
Version control enables tracking infrastructure changes, rolling back updates, and collaboration.
Step 5: Implement CI/CD for Automation
Automate deployment and configuration using a CI/CD pipeline (e.g., Jenkins, GitHub Actions). A typical pipeline includes:
- Terraform plan and apply
- Ansible playbook execution
- Automated testing
- Deployment to production
Automation reduces manual effort and ensures consistency across environments.
Best Practices for Successful IaC Implementation
Following best practices ensures long-term success and scalability of IaC:
- Use Modular Code: Divide Terraform and Ansible code into reusable modules for easier maintenance.
- Implement Secrets Management: Use tools like HashiCorp Vault or AWS Secrets Manager to store sensitive data securely.
- Enable State Locking: Prevent simultaneous infrastructure changes using Terraform state locking.
- Automate Testing: Use tools like Kitchen-Terraform or Molecule to validate infrastructure before deployment.
- Define Role-Based Access Control: Restrict access to infrastructure code based on roles and permissions.
Case Study: Automating Infrastructure for a Financial Services Company
Challenge
A leading financial services company faced challenges with inconsistent infrastructure configurations and slow deployment times.
Solution
- Deployed Terraform for infrastructure provisioning across AWS and Azure.
- Used Ansible to automate application deployment and system configuration.
- Set up a GitHub-based CI/CD pipeline to automate testing and deployment.
Outcome
- Reduced deployment time by 40%.
- Improved system reliability with consistent infrastructure configurations.
- Enhanced security through automated compliance checks.
Conclusion
Infrastructure as Code (IaC) is a powerful approach to managing and scaling infrastructure in a consistent, reliable, and automated manner. By combining Terraform for infrastructure provisioning and Ansible for configuration management, organizations can streamline DevOps automation and reduce operational risks.
Following this guide will enable Waltcorp to establish a robust IaC framework, improve infrastructure consistency, and accelerate deployment cycles. Implementing best practices and automation strategies will position Waltcorp as a leader in DevOps consulting and automation.






